Add Your Heading Text Here
As of today, October 14, 2024, the Cybersecurity Maturity Model Certification (CMMC) program has officially been published in the Federal Register after a lengthy and meticulous four-year development period that involved extensive stakeholder engagement and feedback. This significant milestone marks a crucial step in enhancing cybersecurity standards for organizations within the Defense Industrial Base. The program is set to take effect on December 14, 2024, and businesses should prepare for the upcoming changes. You can expect to see formal assessments beginning in the first quarter of 2025, laying the groundwork for improved security practices across the industry and ensuring that contractors meet established cybersecurity requirements to protect sensitive information. This article provides an overview of the program and the changes that have been implemented. Future articles will explore the program’s nuances in greater detail.
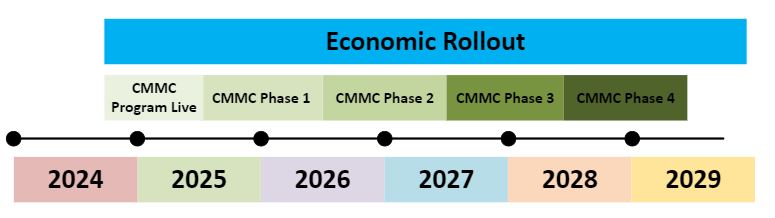
DoD Phased Roll Out
The DoD will roll out the CMMC requirements in defense contractor’s contracts over a phased implementation to alleviate the strain on companies getting assessed and the assessor community. This roll out will be done over a 4 year period with each phase being one (1) year long. The phases will begin when the DFARS 252.204-7021 Clause is published and effective.
Phase 1: On the effective date (2025) of DFARS 7021, the Department of Defense (DoD) plans to mandate that all relevant solicitations and contracts include the requirement for Cybersecurity Maturity Model Certification (CMMC) statuses of either Level 1 (Self) or Level 2 (Self) as a condition for contract award.
Phase 2: Begins one calendar year (2026) following the start date of Phase 1. In addition to Phase 1 requirements, DoD intends to include the requirement for CMMC Status of Level 2 (C3PAO) for applicable DoD solicitations and contracts as a condition of contract award.
Phase 3: The implementation will commence one calendar year (2027) after the start date of Phase 2. In addition to the requirements of Phases 1 and 2, the Department of Defense (DoD) plans to mandate a CMMC Status of Level 2 (C3PAO) for all relevant DoD solicitations and contracts. This will serve as a prerequisite for contract awards and for exercising option periods on contracts awarded after the effective date.
Phase 4: Commencing one calendar year (2028) after the start date of Phase 3, the Department of Defense (DoD) will incorporate CMMC Program requirements into all relevant DoD solicitations and contracts. This includes option periods for contracts awarded before the initiation of Phase 4.
NOTE: This phased implementation pertains to the Department of Defense (DoD) and its prime contracts. There are no rules or regulations prohibiting primes or subcontractors from requiring their subcontractors to obtain CMMC certification for their contracts. This approach helps mitigate risk and ensures that the supply chain is prepared when the DoD conveys its requirements.
Affirmation Requirements
The OSA must affirm continuing compliance with the appropriate level self-assessment or certification assessment. An Affirming Official from each OSA, whether a prime or subcontractor, must affirm the continuing compliance of their respective organizations with the specified security requirement after every assessment, including POA&M closeout, and annually thereafter. Affirmations are entered electronically in SPRS. The affirmation shall be submitted in accordance with the following requirements.
The Affirming Official means the senior level representative within each organization seeking assessment (OSA) who is responsible for ensuring the OSA’s continuing compliance with the specified security requirements for their respective organization.
Each CMMC Affirmation
- CMMC Level 1 (self)
- Annually
- CMMC Level 2 (self)
- At the completion of your Level 2 self-assessment
- Annually
- CMMC Level 2 (3rd Party Certification)
- At the completion of your Level 2 certification
- Annually
- CMMC Level 3 (DIBCAC)
- At the completion of your Level 3 certification
- Annually
ESPs and SPDs
External Service Providers are no longer mandated to obtain CMMC certification if they do not handle any Controlled Unclassified Information. However, if they are processing, storing, or transmitting Security Protection Data, or providing Security Protection Assets, they will be in scope for the assessment requirements for defense contractors.
NOTE: ESPs can choose to undergo a CMMC certification assessment voluntarily, which can help lessen the effort required during the contractor’s evaluation.
Examples of External Service Providers include, but are not limited to:
- Managed Service Provider
- Managed Security Service Provider
- Managed Print Service
- Managed Detection Response
- VoIP Provider
- Door Access Control Provider
- Camera Provider
Security Protection refers to data that is stored or processed by Security Protection Assets (SPAs), which are utilized to safeguard an OSC’s assessed environment. Security Protection Data (SPD) encompasses security-relevant information, including but not limited to:
- Configuration data required to operate an SPA
- log files generated by or ingested by an SPA
- data related to the configuration or vulnerability status of in-scope assets
- passwords that grant access to the in-scope environment
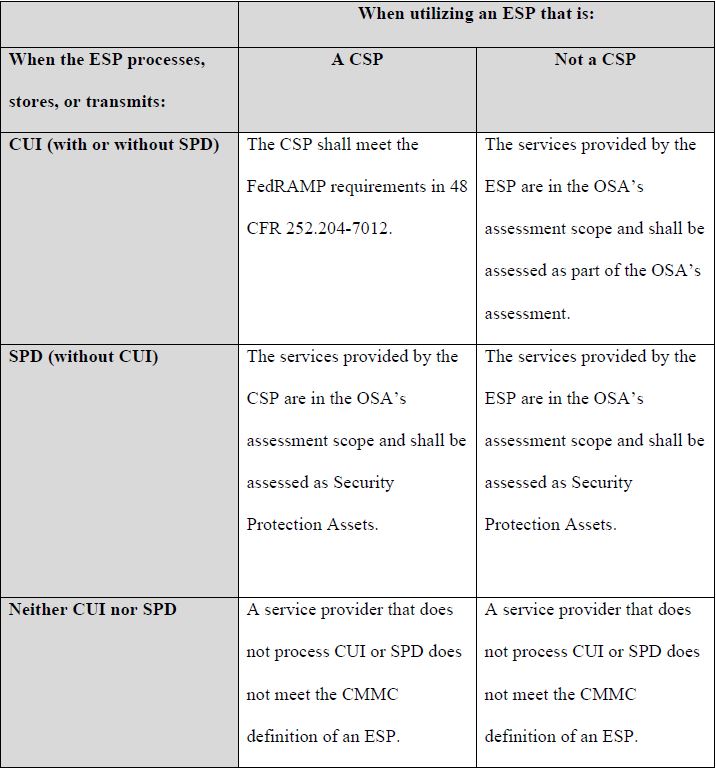
Controlled Unclassified Information (CUI) that is stored, processed, or transmitted in the cloud must be authorized under the Federal Risk and Authorization Management Program (FedRAMP) Moderate framework or an equivalent standard. This requirement is established by the Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012, which emphasizes the importance of safeguarding sensitive information within government contracts. Furthermore, it is crucial to note that Security Protection Assets and Security Protection Data are mandated to have FedRAMP Moderate authorization—or an equivalent standard—only if these assets contain CUI. This ensures that all information classified as CUI is adequately protected against potential threats and vulnerabilities in cloud environments, thereby upholding the integrity and confidentiality of sensitive data.
The Steady March
As the CMMC program rule goes live in December, it’s crucial to remember that this is not just an arbitrary set of guidelines but an essential assessment framework grounded in the requirements outlined in NIST SP 800-171 Rev. 2: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations. This framework is designed to ensure that sensitive data is adequately protected from various threats and vulnerabilities that organizations may face in today’s digital landscape. Achieving compliance is a continuous journey that requires ongoing effort, vigilance, and adaptation, not just a sprint to meet a deadline. It involves regular reviews, updates to security practices, and employee training to stay ahead of potential risks. If you have any questions or need assistance navigating your compliance efforts, don’t hesitate to reach out to Iron Forge Technologies, where our experts are ready to support you every step of the way. Together, we can help you build a robust security posture that meets CMMC requirements and protects your valuable information assets.



